Collective Cyber Security Intelligence
Apple hardware, software, and services work together to give you and your employees the power and flexibility to do whatever needs doing — whether you’re a small business or enterprise.
our products
View Our Products

Endpoint Detection and Response (XDR)
Cross-platform threat prevention and remediation for Windows, Mac and Linux.

Managed Detection and Response (MDR)
CX shield Managed Detection and Response provides powerful and
affordable threat detection and remediation services.

Managed Threat Hunting (MTH)
Threat Hunting is a 24/7 service that proactively identifies and then alerts customers to potential threats before an active attack begins.

DNS Filtering
Block access to known suspicious web domains to secure productivity and collaboration.

Endpoint Detection and Response (XDR)
Preemptively detect and stop phishing threats. Low-touch, high-efficacy threat detection for blocking and isolating malicious content.
Cross-platform threat prevention and remediation for Windows, Mac and Linux.
CX Shield
Endpoint Detection and Response (XDR)

Escalating threats
Over 68% of firms suffered recent attacks and 80% were unknown “zero-day” threats.
Sources: 2020 EDR Solutions Study, Ponemon Institute

Zero-day detection
Almost 60% of firms need zero-day detection, but high false positives are a key concern.

Complex solutions
More than 61% of firms say complexities and limited staff are significant challenges with EDR products.
Three critical EDR features
Detection and protection against ransomware, malware, trojans, rootkits, backdoors, viruses, brute force attacks, and “zero-day” unknown threats that other EDR tools don’t catch.

This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
Easy
CX shield Endpoint Detection and Response for Windows and Mac can easily replace or augment other endpoint security solutions, including Microsoft Defender.
- Non-disruptive, role-based access, deploy within minutes
- Lightweight endpoint agent, robust integrations
- Intuitive cloud-native management console
Effective
CX shield EDR uses unique Anomaly Detection machine learning to not only detect known threats, but also find unknown “zero-day” threats.
- Granular isolation for processes, networks and Windows desktops
- Collects detailed threat information for analysis and investigation
- Proprietary Linking Engine removes executables, artifacts, and changes
Efficient
CX shield EDR offers remote worker optimization, industry-leading efficiency, high return on investment (ROI), and low total cost of ownership (TCO)
- Guided threat hunting to search for Indicators of Compromise (IOCs)
- 72-hour ransomware rollback for Windows workstations
- No performance impact, uses an order of magnitude fewer resources
CX Shield n e x t - g e n E D R t o o l
Innovative active threat response
keeps endpoints productive

Remote worker protection
Our powerful scan and detection engine provides stronger protection against infections from exploits and packaged and polymorphic malware, making it ideal for remote work environments where users may be easier targets.
Low false positive alerts
The average enterprise security team spends over 25 percent of their time chasing thousands of false positive alerts each month (Ponemon).
Automated remediation
Find and reverse all major and subtle changes made by malware.
While traditional approaches focus on removing only the active executable, they ignore residual change that leads to re-infection or pesky PUPs and PUMs. The proprietary CX Shield Linking Engine tracks every artifact, change, and process alteration (including memory executables others miss).
Improved threat detection
Sophisticated attacks exploit entry points and security vulnerabilities, and once attackers are inside, they can set hooks that cause serious damage.
Attack isolation
Desktop isolation alerts the end user of the threat, temporarily blocks their access, yet keeps the device online for analysis.
Ransomware rollback
For Windows environments, paying ransomware is no longer a requirement. If you’re infected, CX Shield simply backs out device changes and restores files that were encrypted, deleted, or modified. And data storage space isn’t an issue, as our proprietary dynamic exclusion technology learns “good” behavior of applications and minimizes storage utilized.

Elevate Threat Prevention for Safer Web Browsing
Keep threats originating from nefarious websites, web-based apps, or online content from wreaking havoc in your organization. Deliver end users a safer, more productive web experience with our DNS Filtering module for our cloud-based Nebula platform.
See our powerful business solutions in action
Watch a CX shield Product Demo and see how we protect large and small businesses from ransomware, malware, viruses, and other emerging threats. We’ll show you how to secure your organization with a few simple clicks.
CX shield Managed Detection and Response provides powerful and
affordable threat detection and remediation services with 24×7
monitoring and investigations, purpose-built for resource constrained IT teams.
Managed Detection and Response (MDR)

Boost constrained team resources
Lack of bandwidth and skills can limit the ability of your team to effectively monitor and react to threat alerts. CX Shield MDR Analysts fill these gaps 24×7 and become an extension of your team.

Free your team from alert fatigue
Never ending cyber-attacks continually flood organizations with threat alerts. CX Shield MDR monitors and triages threats on your behalf, freeing your team.

Reduce dwell time of hidden threats
Lengthy dwell times lead to greater risk of infection. CX Shield MDR hunts down hidden threats based on suspicious activity and past IOCs, reducing dwell time and potential impact of hidden threats.
Powerful and affordable threat detection and remediation
- 24×7 alert monitoring and guidance for MSPs to help eliminate threats using the power of CX Shield EDR remediation
- Check Mark Threat hunting across customer sites, helping to prevent hidden threats from becoming active infections
- Check Mark Managed antivirus on CX Shield EDR, supporting enhanced security posture

24×7 Alert Monitoring
As a 24/7 global security operations center (SOC), we monitor and investigate alerts across customer endpoints day and night, rapidly triaging the most critical threats.

Remediation Your Way
Our MDR Team can actively remediate threats as they are discovered OR provide highly actionable guidance for your team to follow in their own remediation efforts. It’s your choice.

Threat Hunting
Our MDR Team hunts unseen threats based on past indicators of compromise (IOCs) and suspicious activity observed on endpoints.

Skilled MDR Analysts
Our team of security experts are accomplished threat hunters and incident responders with decades of combined experience triaging and mitigating complex malware threats.
Why MDR Matters to your Organization
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
60%+
Over 60% of security teams admit to lacking sufficient staff to meet the security needs of their organizations.
ISC 2021 Cybersecurity Workforce Study
$4.87M
Data breaches that took longer than 200 days to identify and contain cost on average US $4.87 million, compared to $3.61 million for breaches that took less than 200 days.
Ponemon Institute
287 Days
According to Ponemon Institute, the average number of days that an organization takes to identify and contain a data breach is 287 days.
Ponemon Institute and IBM Security. Cost of a Data Breach Report. 2021
Managed Threat Hunting (MTH) is a 24/7 service that proactively identifies and then alerts customers to potential threats before an active attack begins. Using threat intelligence, MTH hunts for events and indicators of the concern or compromises (IOCs) that are hidden, overlooked or were previously unknown.
Identify Hidden Intruders Before They Attack
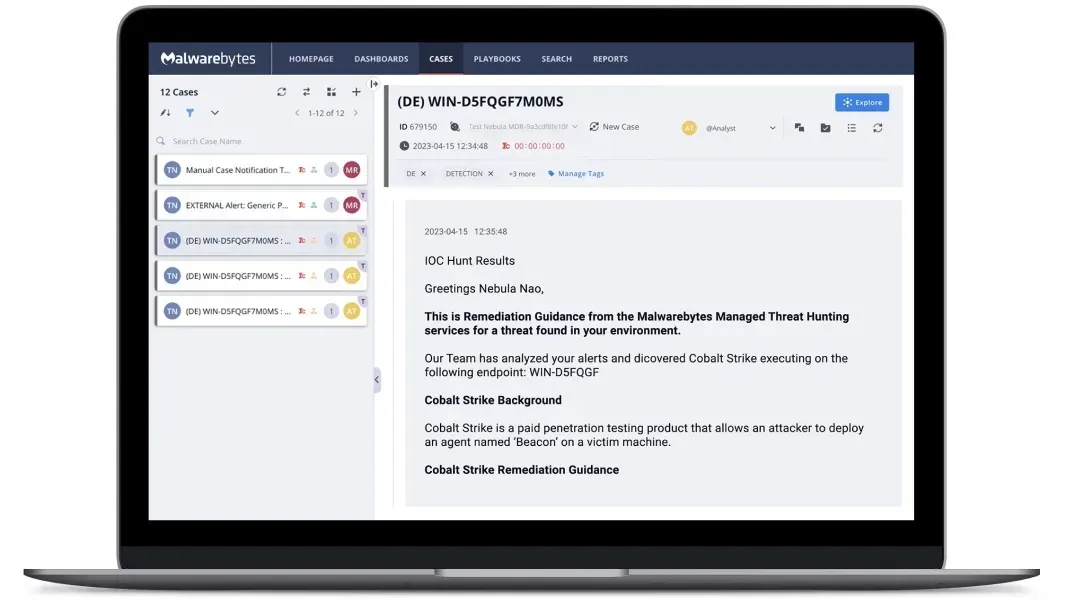
Never miss another threat
Managed Threat Hunting (MTH) is essential to stop intrusions that evade remediation and cause the greatest damage.
When a threat hunt results in a positive finding, the customer is notified and sent IOC specific guidance with their investigation and remediation.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
20%
of attacks evade detection by automated security tools – and cause the majority of damage.
IBM Security – Master Threat Hunting Report – 2018
91%
of organizations report improvements in speed and accuracy of response due to threat hunting.
SANS Institute
80%
of endpoint security alerts ignored. Organizations that monitor their network suffer from security alerts fatigue and fail to recognize IOCs.
21 day
intruder dwell times lead to severe breaches. The more indicators of concern or compromise that are missed, the longer a cybercriminal can lurk in your network.
TCX shield n e x t - g e n E D R t o o l
Benefits

Never miss another threat
Guided notifications add a layer of visibility into endpoint security alerts, surfacing the most critical IOCs to the attention of IT staff.
Cut time and cost of remediation
By escalating specific incidents for review, MTH accelerates threat response times, reducing the cost of remediation, potential downtime, and recovery.
Avoid new security hires
MTH adds and extra layer of expertise against ransomware and other advanced threats, at a fraction of the cost of new hires.
Reduce stress on IT staff
MTH eliminates the stress of dealing with volumes of alerts and missed threats by using threat intelligence to hunt for critical indicators of concern of compromise.
Mitigate the risk of breach
MTH finds hidden intruders sooner, reducing their dwell time and potential for damage, which mitigates the risk of a crippling breach.

Proactive Hunts
MTH leverages internal and external threat intelligence to seek out hidden threats before a new attack can begin.

Guided Notifications
Customers receive guided notifications, based on severity of threat and type of IOC, to help with their investigation and remediation.

Integrated with EDR
MTH is purpose-built for CX Shield EDR (Endpoint Detection and Response) customers and MSPs (Managed Service Providers).

Integrated with MDR
MTH is included in CX shield MDR (Managed Detection and Response) for customers who need 24/7 network monitoring, investigation, remediation, and threat hunting in one service.
Block access to known suspicious web domains to secure productivity and collaboration.
DNS Filtering

Easily deliver safer, more productive web access
Threats come from many sources, and CX Shield customers trust us to prevent infections across vectors. Our DNS Filtering module extends our cloud-based security platform, blocking sites that introduce risk and impede productivity so you can better protect end users and your web-based applications.
Isolate the deep, dark corners of the web
For all its practical uses, the web is also a common source of phishing attacks, spyware, common viruses and malware, not to mention ransomware. DNS Filtering allows you to block whole categories of inappropriate sites, known, suspicious domains, and other nefarious content from wreaking havoc across your business. Ultimately, you want to ensure your end users are more safe and productive on the web.
Block threats from infiltrating browsers and web-based apps
With our DNS Filtering module, you’re able to block whole website categories such as gambling, adult content, etc. Gain access to an extensive database of pre-defined scores on known, suspicious web domains and manage specific site restrictions. Beyond browsing, you’re able to better protect the web-based applications that run your operations, keeping your end users safe and productive.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.

Safe, productive web access
You want end users to be able to access websites and online content they need to get work done. But you need to keep your organization safe against cyberthreats.
Benefit from an extensive database of known, suspicious web domains, so you can easily deploy restrictions against these and whole categories of websites that don’t comply with your organization’s code of conduct policies for internet use.
Protect web-based systems

Web-based apps are central to your organization’s mission, and you need to ensure these collaborative systems do not introduce threats to your digital ecosystem.
You may not have a complete picture of vendor and partner security posture, so you need prevention that keeps your shared databases and systems from being exposed to threats introduced from their environment.
Prevention aids compliance

Industry regulations or other mandates require organizations to demonstrate cyberprotection against several threat vectors. But they don’t always define how to do it.
Adding our DNS Filtering module helps you on the path to compliance with protection from threat actors lurking on the internet. Coupled with our cloud-based EDR platform, you’re well on your way to demonstrating compliance with HIPAA, GDPR, CIPA, and other industry requirements.
CX Shield MDR service
protects your business and
responds to incidents 24×7—so you don’t have to
CX shield Managed Detection and Response (MDR) provides powerful and affordable threat detection and remediation services with rapid set-up and 24×7 monitoring and investigations. Our top-tier MDR Analysts protect your organization from cyberthreats through accelerated threat detection and response to incidents—allowing you to focus on growing your business.
Preemptively detect and stop phishing threats. Effortless protection against email-borne malware, business email compromise (BEC), and multi-channel (link- and QR-based) phishing attacks. Low-touch, high-efficacy threat detection for blocking and isolating malicious content.
Cloud Email Security
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
This is a paragraph. Writing in paragraphs lets visitors find what they are looking for quickly and easily.
Phishing protection goes beyond email
Protect against targeted phishing attacks that use a combination of email and other collaboration apps to exploit users and gain unauthorized access.

Low-touch, high-efficacy threat detection
Realize industry-leading threat detection efficacy without having to constantly tune policies and configurations.
Greater value, lower cost
Save time, money, and your sanity — all while catching the phishing threats that others miss

Cloudflare named a “Leader” in the 2023 Forrester Wave for Enterprise Email Security
In its 2023 market analysis focused on email security, Forrester highlighted Cloudflare’s delivery of in-line and API-enabled email security capabilities to thwart multichannel phishing, ease and speed of investigation, and ability to protect users before, during, and after email delivery.
Top use cases
Block and isolate multi-channel attacks — Insulate employees from link-based attacks that exploit users across various applications, including QR code and deferred attacks.
Stop business email compromise (BEC) — Detect highly-deceptive attacks that impersonate employees and vendors using leverage impersonated and compromised accounts to steal information and extract fraudulent payments.
Prevent ransomware and other malware-based attacks — Block dangerous attachments and links that attempt to deploy malicious software on end-user devices.
Protect users before, during, and after email delivery —
Deliver continuous protection against known and emerging phishing tactics, even those cleverly designed to evade traditional email security controls.
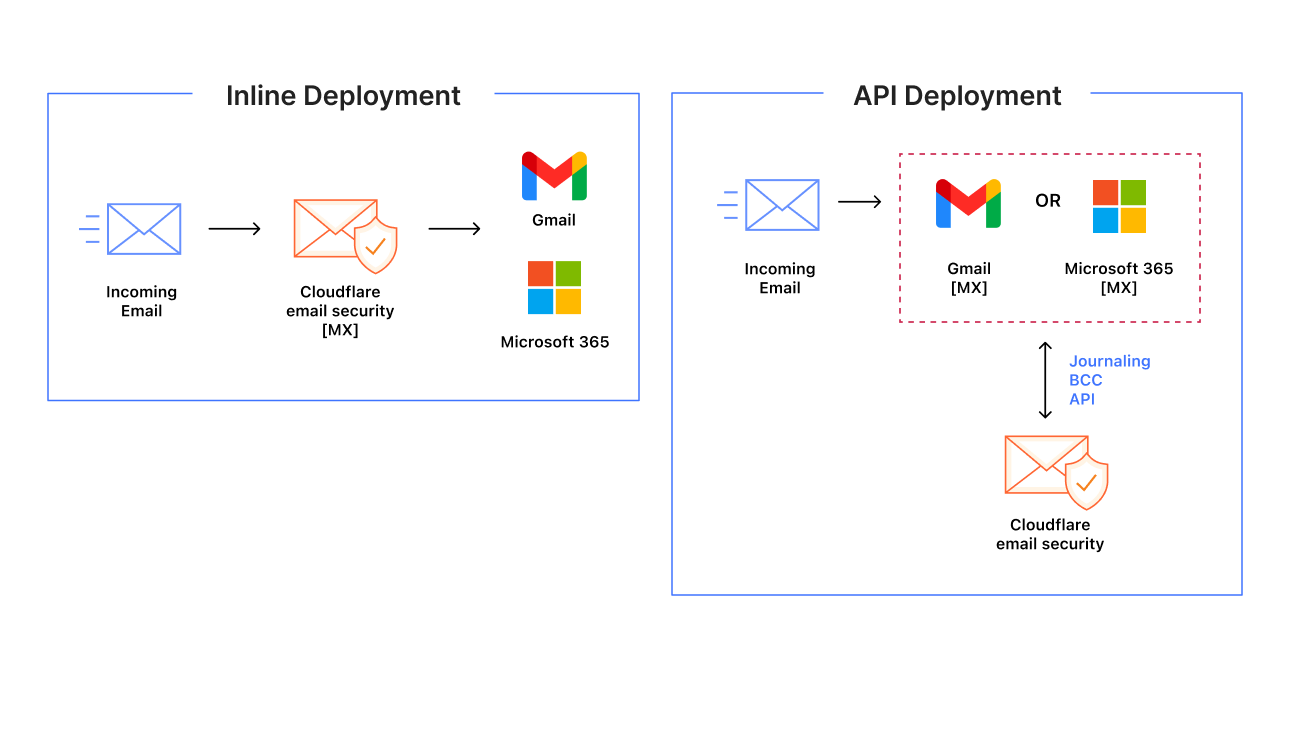
How it works
- (M365 users) Run a free phishing retro scan in minutes to identify active threats that have already evaded existing security controls over the past 14 days and are currently sitting in your inboxes. (Gmail users) Request a free phishing risk assessment to identify the phishing threats that are evading your existing security controls, as they’re being delivered.
- Review the results of your scan or assessment to better understand the frequency and types of attacks that are bypassing your current defenses.
- Deploy Cloudflare’s email security service either inline (as MX), via API, or in multi-mode (hybrid of both).

Extend your phishing protection – without disrupting users
Cloudflare’s email security service, as part of a unified Zero Trust platform, protects against phishing campaigns that go beyond email to exploit your most valuable resource – people. With innovative methods for detecting and mitigating user-targeted attacks, Cloudflare delivers invisible protection that extends to the full suite of applications that support both office and remote employees.
By layering Cloudflare on top of your cloud email provider, you can augment your existing email capabilities while securing both users and applications with a single, composable security platform.
